Server_status Revenge
First time solving a race condition / shared memory CTF challenge.
Reverse Engineering#
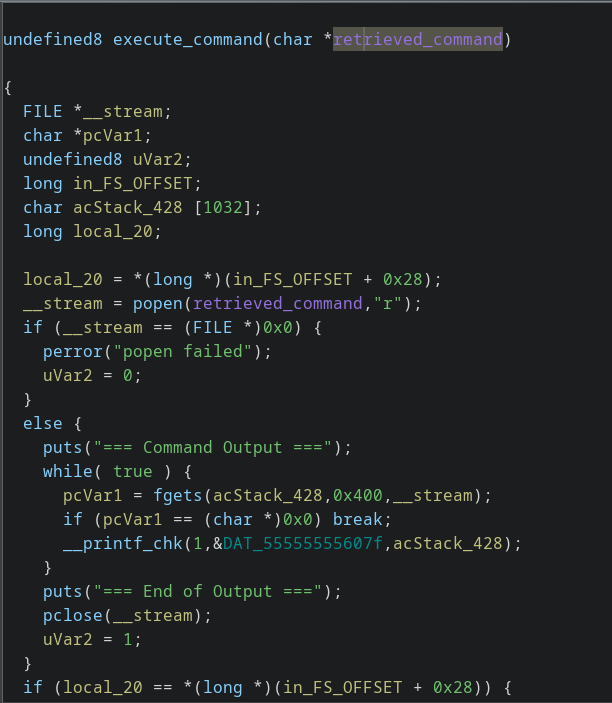
Login to the instance, and download the challenge binary. Open it up in ghidra shows
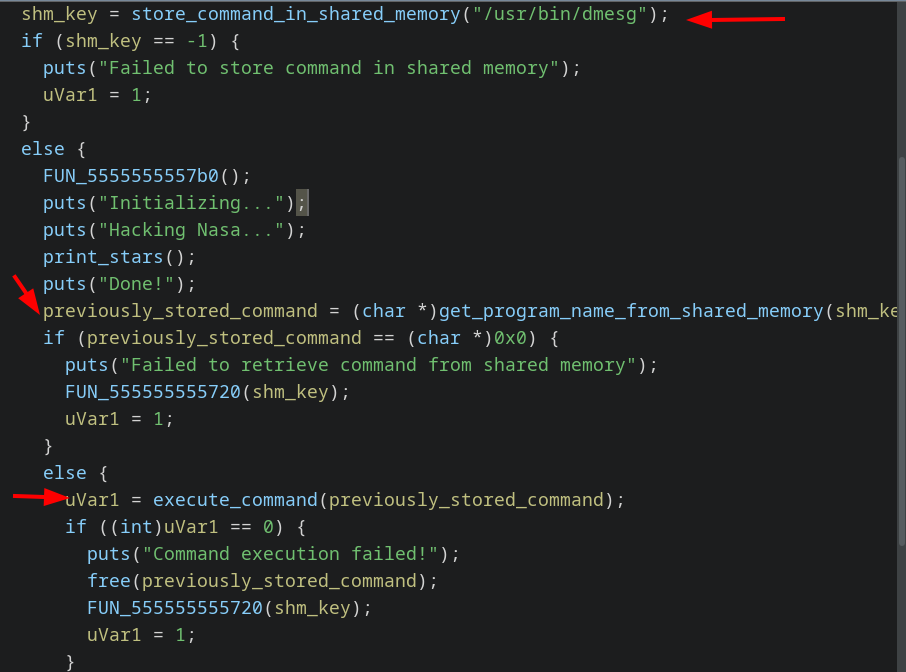
What is happening#
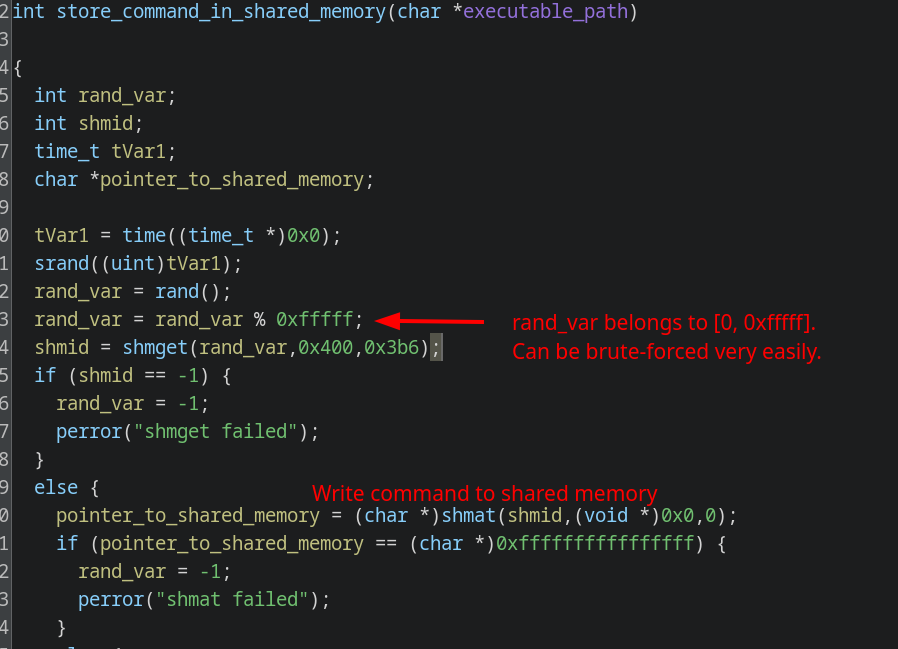
- Store command in shared memory obtained by using a weak shmid.
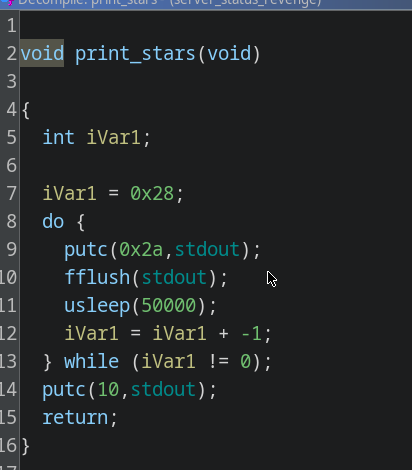
- Display a loader for about 1.5 secs
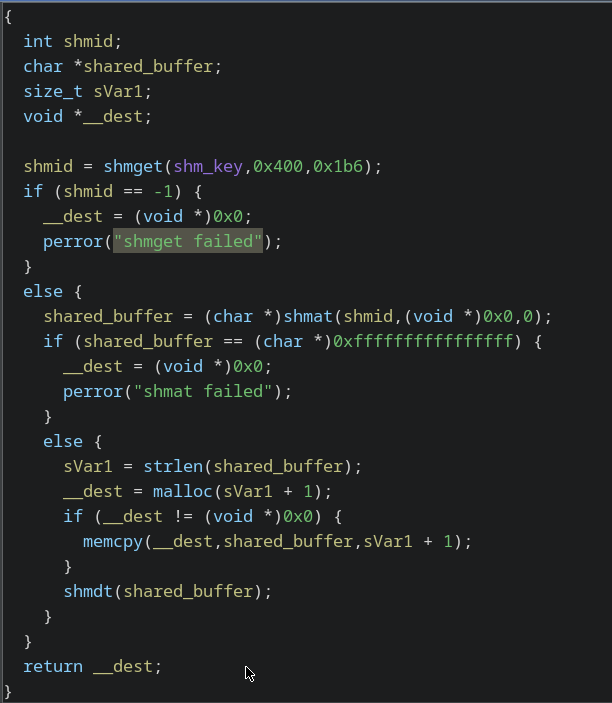
- Retrieve command from shared memory.
popenit
Exploit#
The following C Code:
- Get’s handles to shared memory in the range [0, 0xfffff].
- Writes the string to it.
C
| |
Copy the exploit to the instance, and right after executing ./secure-server, execute the exploit.
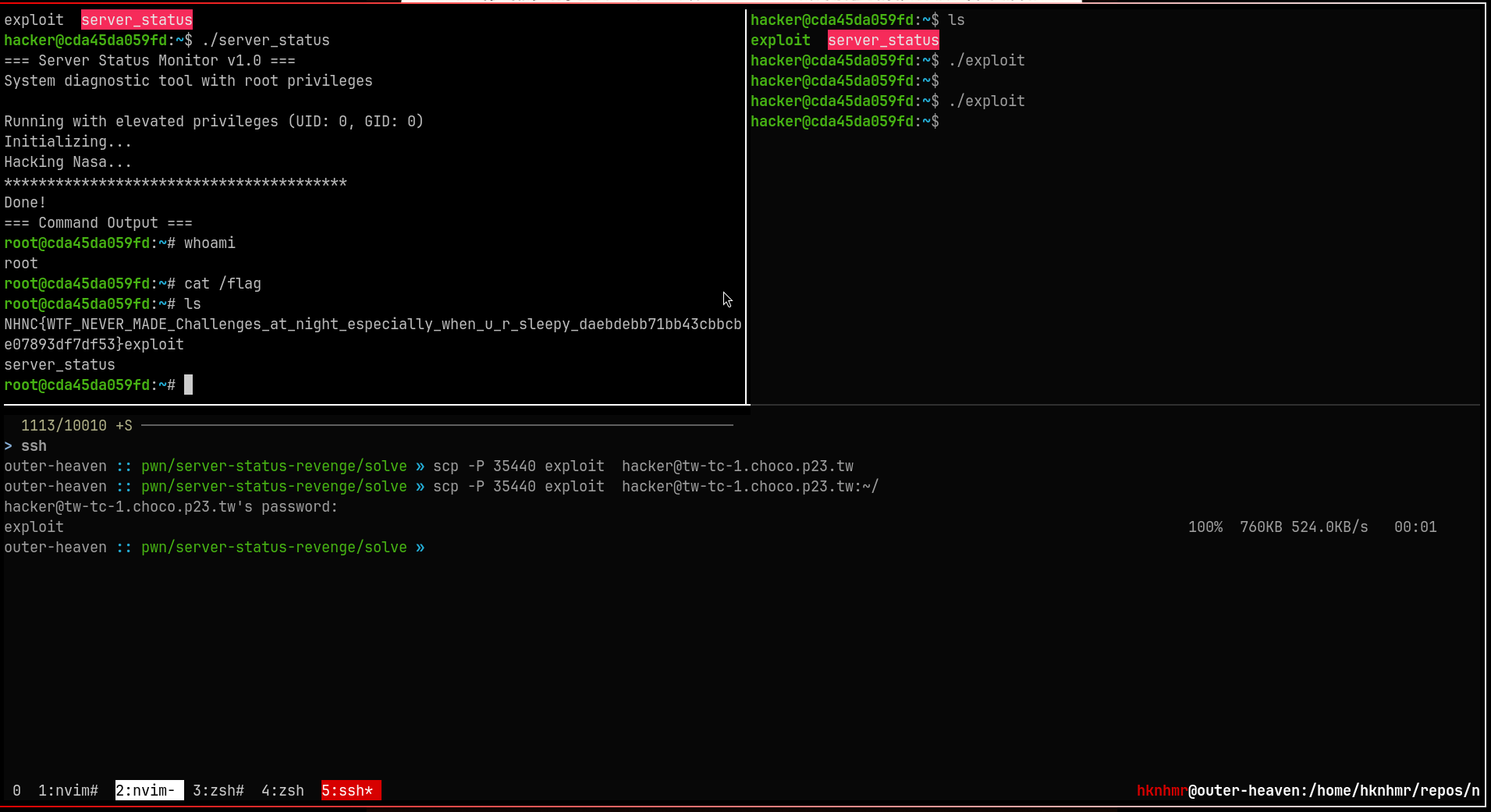
Flag#
The flag content is referring to server-status challenge
NHNC{WTF_NEVER_MADE_Challenges_at_night_especially_when_u_r_sleepy_daebdebb71bb43cbbcbe07893df7df53}